The adventure of water sports, from the smooth mood of swimming to the adrenaline surge of surfing, coaxes many, particularly throughout the late spring months. For the people who have gone through laser hair removal, the possibility of partaking in these oceanic exercises with newly discovered certainty is tempting.
Nonetheless, a key thought emerges: could you at any point jump into water sports not long after your Victoria House Clinic laser hair removal treatment? In this aide, we investigate the elements of participating in swimming, surfing, and other water-related pursuits post-laser hair removal, revealing insight into when it’s protected to stir things up and what safety measures to take to guarantee ideal outcomes and skin wellbeing.
It is by and large not prescribed to swim, including water sports like swimming and surfing, for 24-48 hours after laser hair removal.
The treated region will be delicate during this time and contact with water can cause bothering or infection. However, after the underlying 24-48 hours, it is protected to swim and appreciate
water sports.
Safeguards I Ought to Take Prior to Going To The Ocean side After Laser Hair Removal
Prior to daring to the ocean side subsequent to going through laser hair removal, it’s crucial for take a progression of precautionary measures to safeguard your treated skin and guarantee the most ideal result. Here is a thorough rundown of insurances to consider:
Sit tight for Mending: Permit adequate time for your skin to recuperate after the laser hair removal treatment. Ordinarily, holding up somewhere around 1 to about fourteen days prior to going to the ocean side is suggested, however counsel your expert for explicit direction in view of your skin type and the power of the treatment.
Sunscreen as Your Safeguard: Apply a wide range sunscreen with a high Sun Security Component (SPF) to all uncovered region of your skin. Ensure the sunscreen offers insurance against both UVA and UVB beams. Reapply at regular intervals, particularly in the wake of swimming or perspiring.
Defensive Attire: Settle on baggy, light-shaded dress that covers the treated regions. Wearing long sleeves, wide-overflowed caps, and shades can give an additional layer of insurance against the sun’s unsafe beams.
Look for Shade: Track down concealed regions at the ocean side to limit direct sun openness. Particularly during top sun hours from 10 a.m. to 4 p.m., remaining in the shade can altogether decrease the gamble of burn from the sun and skin harm.
Stay away from Boiling Water and Steam: Avoid hot tubs, saunas, and other intensity actuating exercises that can make your skin become flushed or aggravated. These exercises can compound the awareness of laser-treated skin.
Avoid Unforgiving Peeling: Shun utilizing brutal exfoliants or cleans on your treated skin prior to going to the ocean side. Peeling can build the gamble of aggravation and make your skin more powerless against the sun’s belongings.
Saturate: Apply a delicate, hydrating cream to your treated skin prior to making a beeline for the ocean side. All around saturated skin is stronger and less inclined to aggravation from the sun and saltwater.
Stay away from Chlorine and Saltwater: While pools and the sea might be enticing, staying away from chlorinated pools and saltwater for the main little while after your laser treatment is fitting. These waters can additionally aggravate delicate skin.
Remain Hydrated: Drink a lot of water to remain hydrated. All around hydrated skin mends all the more effectively and is less helpless to burn from the sun and aggravation.
Counsel Your Specialist: Assuming that you feel a little uncertain or worries about making a beeline for the ocean side after laser hair removal, counsel your expert. They can offer customized exhortation in light of your treatment particulars and skin type.
By sticking to these safety measures, you can partake in your time at the ocean side while defending your skin’s wellbeing and the progress of your laser hair removal treatment. Recollect that persistence and cautious assurance are vital to accomplishing the ideal stylish outcomes without undermining your skin’s prosperity.
 Nowadays metal roofs come in numerous and exciting, colours, shapes and textures. Thi
Nowadays metal roofs come in numerous and exciting, colours, shapes and textures. Thi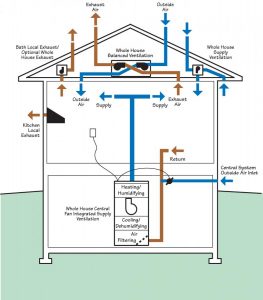 Many issues have been identified as lack of knowledge regarding fan installations or simply a misunderstanding of regulations. An example of a jet fan system installed and investigated involved, quite correctly, two axial main extract fans installed in parallel discharging into a common plenum; however they were installed without non-return dampers fitted to the fans. If one of these fans were to fail, the result would not only be in the loss of performance from the failed fan, but also severely reducing the effectiveness of second fans performance due to air short-circuiting through the failed fan.
Many issues have been identified as lack of knowledge regarding fan installations or simply a misunderstanding of regulations. An example of a jet fan system installed and investigated involved, quite correctly, two axial main extract fans installed in parallel discharging into a common plenum; however they were installed without non-return dampers fitted to the fans. If one of these fans were to fail, the result would not only be in the loss of performance from the failed fan, but also severely reducing the effectiveness of second fans performance due to air short-circuiting through the failed fan.